Setup MySQL on Ubuntu
Setup MySQL
Setup PHP on NGINX
Setup PHP
- Add the below software and repository
> sudo apt-get install software-properties-common
> sudo add-apt-repository ppa:ondrej/php
> sudo apt-get update - Install PHP 7.1
> sudo apt-get install php7.1
- Install common PHP modules
> sudo apt-get install php7.1 php7.1-cli php7.1-common php7.1-json php7.1-opcache php7.1-mysql php7.1-mbstring php7.1-mcrypt php7.1-zip php7.1-fpm
- Edit the php.ini file
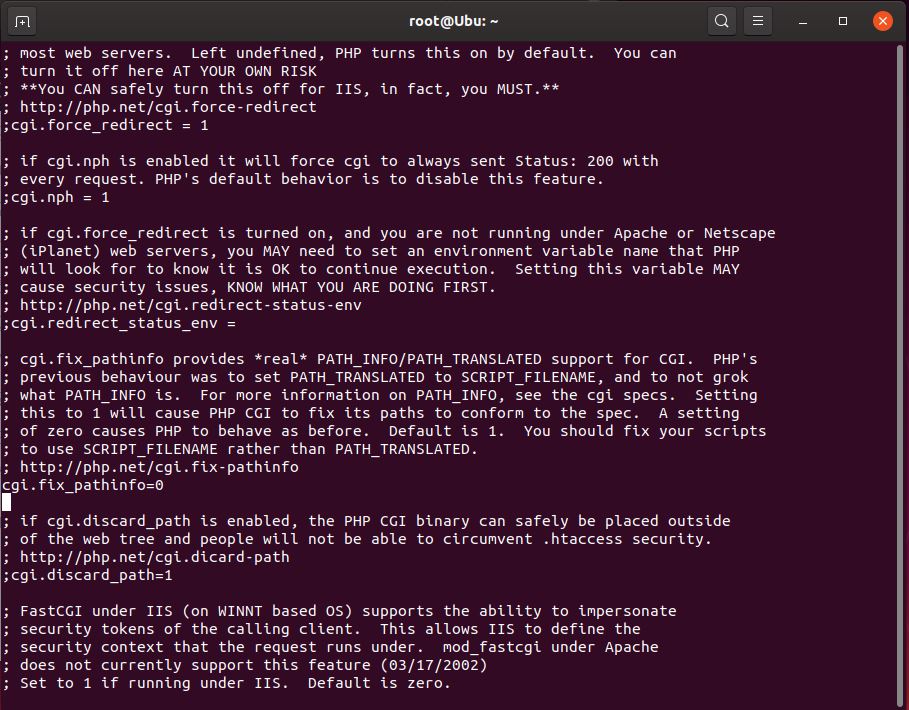
> sudo vi /etc/php/7.1/cli/php.ini - in the php.ini file type /cgi. and hit enter to find the below line and edit
cgi.fix_pathinfo=0
- Restart the PHP 7.1 service
> sudo service php7.1-fpm restart - Edit the NGINX config to enable PHP
> sudo vi /etc/nginx/sites-enabled/default
Remove the comments from the below php settings
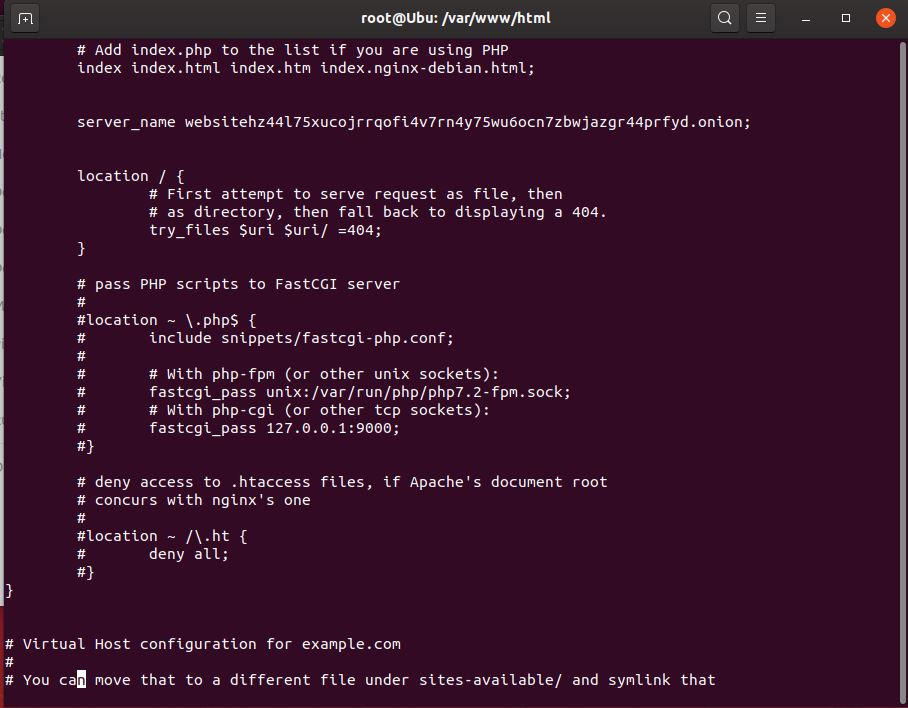
- Restart nginx service
> sudo service nginx restart - Enable PHP and nginx to start on reboot
> sudo systemctl enable nginx.service
> sudo systemctl enable php7.1-fpm.service
Use custom .onion address
Changing generic onion to one generated earlier
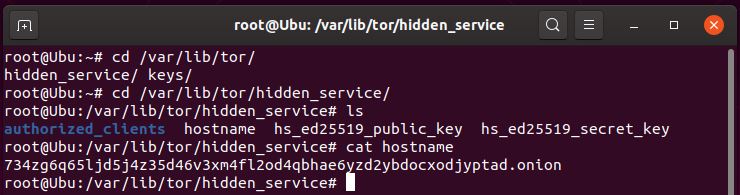
- Check the current .onion generated when you first setup TOR (in case you want to use it)
> cd /var/lib/tor/hidden_service/
> cat hostname
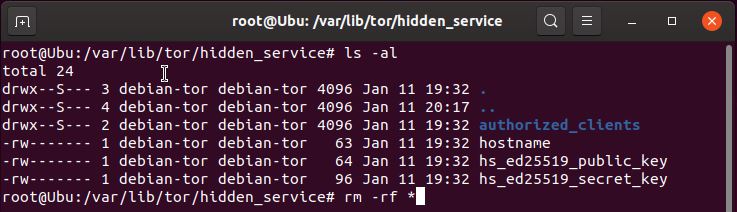
- If you wish to use a custom address, delete (or move) the old keys
> cd /var/lib/tor/hidden_service/
> rm -rf *
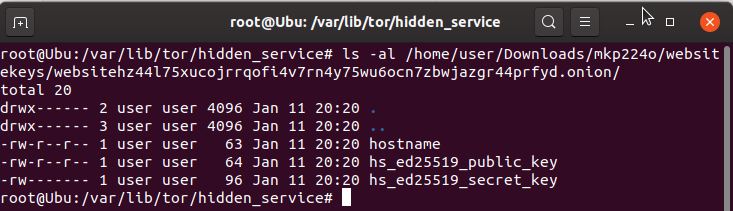
- locate the keys to copy
> cd /home/<your username>/Downloads/mkp224o/<key folder name>/<key folder>/
example
> cd /home/user/Downloads/mkp224o/websitekeys/websitehz44l75xucojrrqofi4v7rn4y75wu6ocn7zbwjazgr44prfyd.onion/
> ls -al
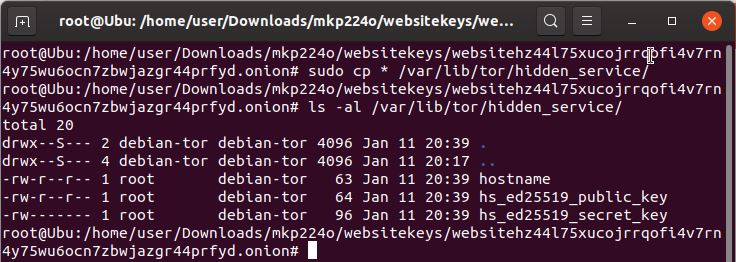
- Copy the generated keys to the onion service location
> sudo cp * /var/lib/tor/hidden_service/
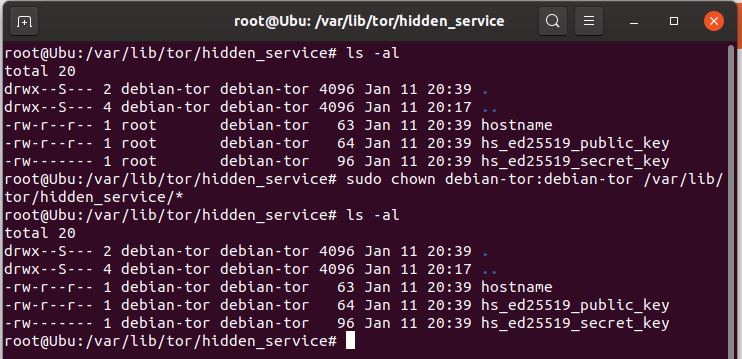
- change ownership of the copied keys so the service can access them
> sudo chown debian-tor:debian-tor /var/lib/tor/hidden_service/*
- restart the tor service
> sudo service tor restart
How to create a .onion Web Server
Setup NGINX from the APT repository
-
> sudo apt install nginx
-
Edit the web server config to link it to tor listening on port 80
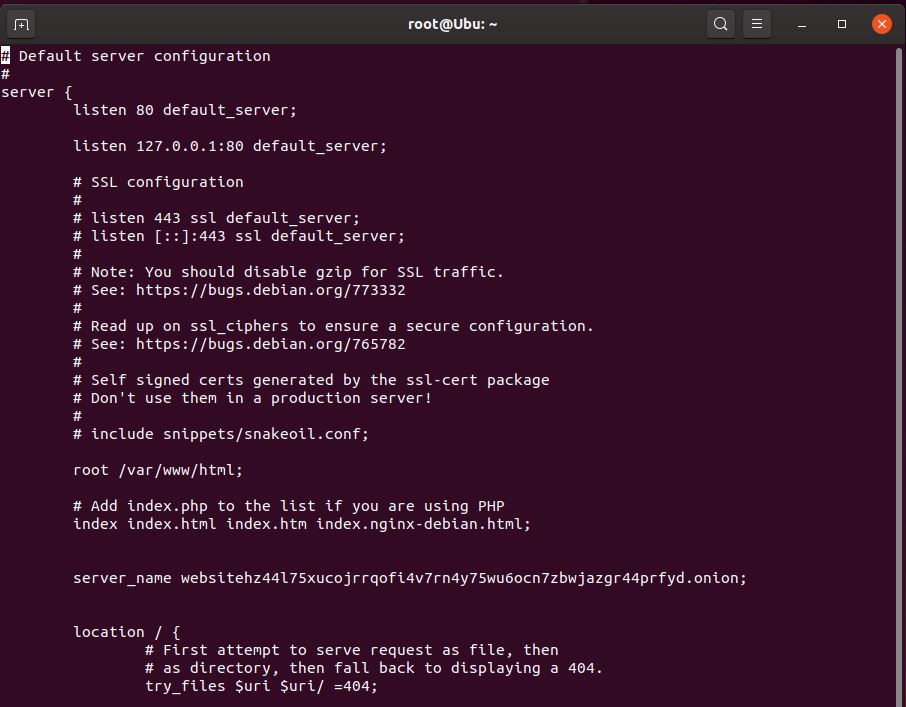
> sudo vi /etc/nginx/sites-enabled/default -
Change the listen (so it only points to 127.0.0.1) and server name (points to onion address) in the config
- Restart nginx service
> sudo service nginx restart
Setting up the Website
- go to /var/www/html and delete the files there
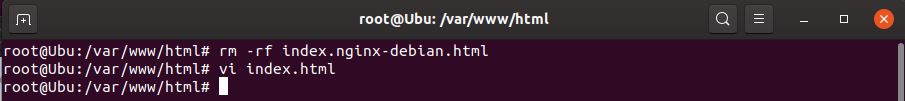
- create a test file and test the web address
> vi index.html
type in some text and save the file - Visit the website and confirm its accessible (your address should be different)
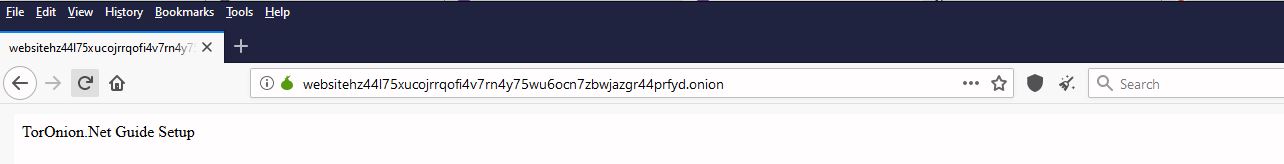
how to secure a .onion server
Change OS Host DNS to run through TOR
- > VirtualAddrNetworkIPv4 10.192.0.0/10 AutomapHostsOnResolve 1 TransPort 9040 TransListenAddress 127.0.0.1 DNSPort 53
- Change Name Server
> vi /etc/resolv.conf
> nameserver 127.0.0.1
> sudo service network restart
Secure NGINX
- https://geekflare.com/install-modsecurity-on-nginx/
- https://www.rosehosting.com/blog/how-to-secure-your-lemp-stack/
Using Knockd for remote access
- https://www.techrepublic.com/article/how-to-obscure-open-ports-with-knockd/
How to create a .onion service
For a .onion server you will need to have a linux server, in this example we will use Ubuntu (u can use the same server we setup to generate the address, or use a third party such as AWS, Azure or Alibaba Cloud)
Installing the Services
- install TOR using APT
> sudo apt install tor - Confirm that Tor is up and running on port 9050 by using the ss command
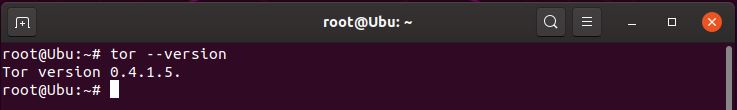
> ss -nlt - check to see if you are using the latest TOR version
> tor –version
- check to see if you are using TOR
this will show your public IP
> wget -qO – https://api.ipify.org; echothis will show your TOR IP
> torsocks wget -qO – https://api.ipify.org; echo



Setting up the Server
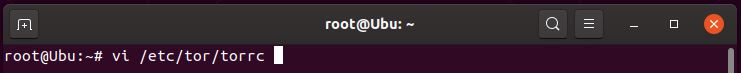
- Edit the torrc file (config file for tor services)
> vi /etc/tor/torrc
- scroll down the page using the arrow keys on the keyboard until you find the lines:
#HiddenServiceDir /var/lib/tor/hidden_service/
#HiddenServicePort 80 127.0.0.1:80 - uncomment (remove the #) from the 2 lines so it looks like below
HiddenServiceDir /var/lib/tor/hidden_service/
HiddenServicePort 80 127.0.0.1:80
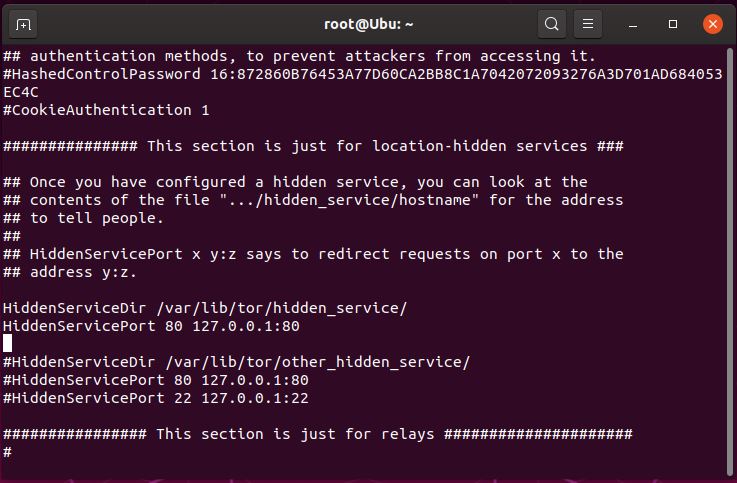
- Save the config by pressing the “Esc” key and typing :wq (write, quit) and hit the “Enter” key
> :wq
- restart the service
> sudo service tor restart

How to create a .onion address
.onion addresses are no longer short (v2) 16 generated characters but are now using 56 characters under version 3.
Old .onion address – yyhws9optuwiwsns.onion
New .onion address – hello23twa7k536qggxfeqm4orwohwlca3ln6f43b4splcym57msaxid.onion
You can use a generator to make a more legible .onion address using the below method, but at this stage the method is only supported under linux.
– Note: Generating your own name isnt REQUIRED, as you can use the default generated when setting up the tor service.
Create a Linux Virtual Machine to Generate a vanity address generator for a ed25519 onion services.
- Install Hyper-V (free) on your Windows 10 machine -> https://docs.microsoft.com/en-us/virtualization/hyper-v-on-windows/quick-start/enable-hyper-v
- Download Ubuntu Desktop -> http://releases.ubuntu.com/19.10/ubuntu-19.10-desktop-amd64.iso
- Install Ubuntu on the Hyper-V -> https://www.windowscentral.com/how-run-linux-distros-windows-10-using-hyper-v
Using mkp224o to generate the .onion address
- Download mkp224o from Github -> https://github.com/cathugger/mkp224o/archive/master.zip
- through GUI or Terminal, extract the .zip to the Ubuntu installation.
> unzip mkp224o-master.zip - Generate the configure script
> ./autogen.sh - configure the make script before compiling
>./configure –enable-amd64-51-30k –enable-intfilter –enable-binsearch –enable-besort - build the binary to generate the .onion addresses
> make
Be aware to generate a bunch of addresses, can take hours or weeks, use the below code and when generating will create a folder of the .onion address, which will include the private and public key for use
note the keys are in binary form and cannot be read in a text editor
> ./mkp224o <beginning text> -B -S 5 -j 16 -d keys
-B = use batching (generate a large number or sets)
-S = print statistics every # of seconds… in this case, every 5 seconds
-j = number of threads to use in the CPU
-d = directory to store the generated keys
e.g
> ./mkp224o website -B -S 5 -j 16 -d websitekeys


















